How do you categorize and prioritize the numerous threats?
How do you tackle these threats using existing tools and data?
In 2013, MITRE used real-world observations to develop the ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) framework, used to categorize adversarial threats and behaviors.
It is an open source, comprehensive list of known attacker behaviors, compiled and separated into tactics and techniques, and structured in multiple easy-to-follow matrices.
MITRE ATT&CK takes the adversaries perspective to help organizations understand how adversaries approach, prepare for, and successfully execute attacks. This is beneficial for organizations to adopt the MITRE ATT&CK framework in order to gain insight into attacker behavior so they can improve their own defenses accordingly.
Key MITRE ATT&CK Terminology
Let's take a quick look at the MITRE ATT&CK terminology, since these terms can often have different meanings for different organizations.
- Tactics: Describes the immediate technical goals of the attackers, such as gaining Initial Access, maintaining Persistence, or gaining Command and Control. To successfully complete an attack, attackers must use multiple tactics.
- Techniques: This describes the methods used by the attackers to achieve a tactic. All tactics in each matrix have numerous techniques associated with them. Some techniques can be broken down further into sub-techniques.
- Procedures: Describes either the specific implementations of techniques and sub-techniques or it can refer to specific malware or other tools attackers have used.
How can Splunk help?
Splunk offers numerous ways to utilize the knowledge and experience curated by MITRE. Below we will take a look at how Splunk's Enterprise Security (ES) App and the Splunk Security Essentials App can assist with the deployment of MITRE ATT&CK use-cases.
Splunk Enterprise Security (ES) 6.4+ and the MITRE ATT&CK Framework
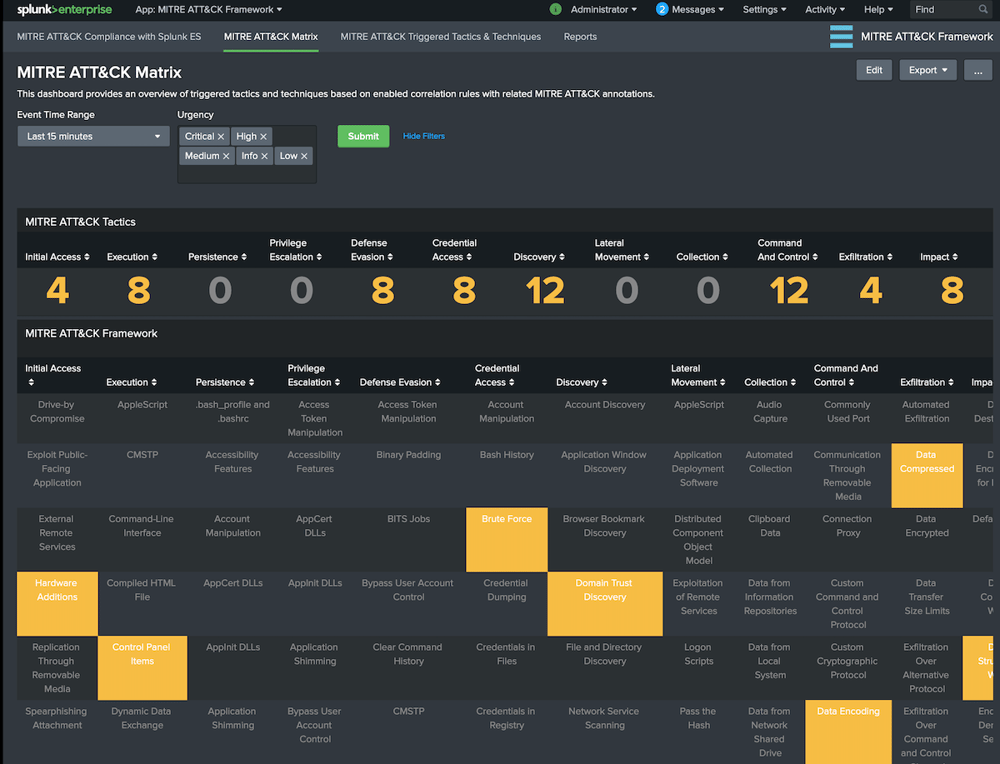
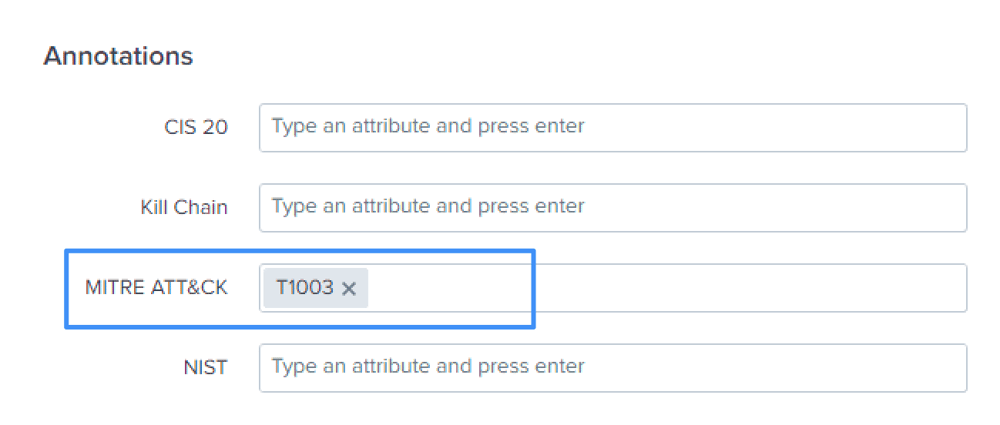
Use Splunk ES's built-in correlation searches to map specific MITRE ATT&CK TTPs (Tactics, Techniques, and Procedures) to notable events/alerts. As of Splunk ES 6.4+, you can now tag the Correlation Searches with their associated MITRE AT&CK tactic number in the configuration page.
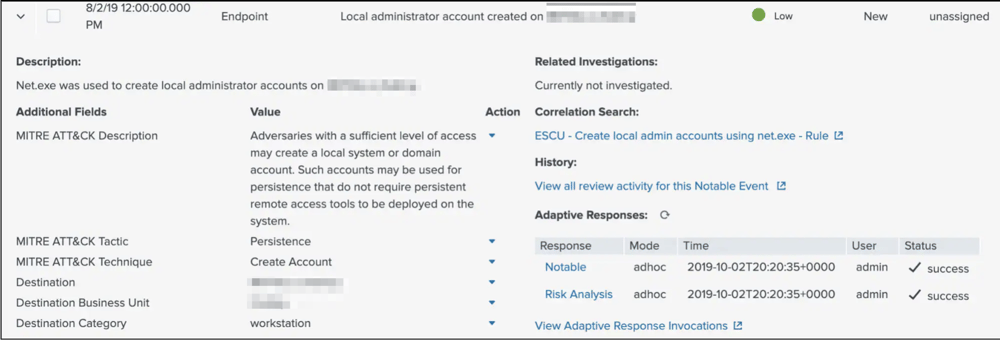
You can then view the resulting Notable Events in Incident Review dashboard that allows you quickly triage, assign, and track issues associated with the MITRE ATT&CK framework.
Security Essentials 3.1+ and the MITRE ATT&CK Framework
Organizations can utilize the Security Essentials app with embedded MITRE ATTT&CK features to reduce complexity, enhance collaboration within security teams and validate migration and remediation capabilities.
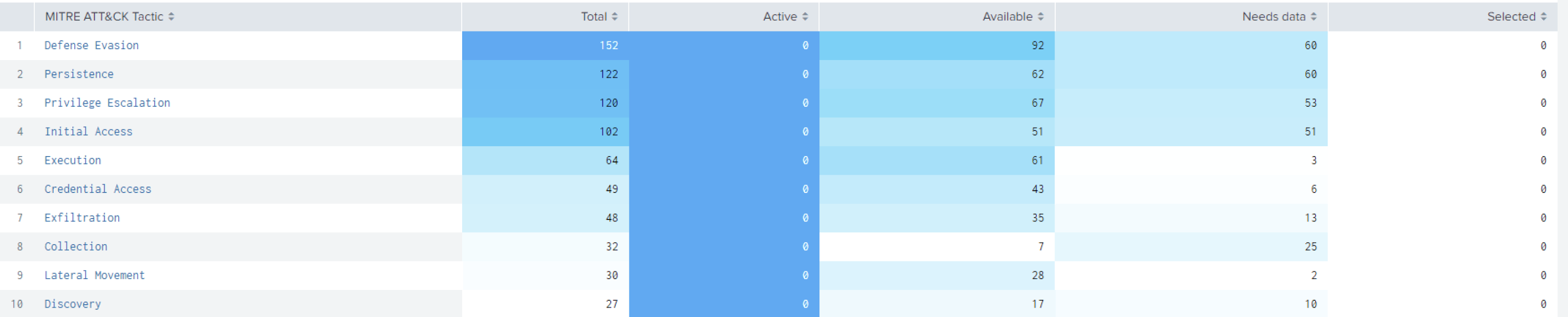
As you can see below, you can use many of the provided filters to zoom in and visualize the MITRE ATT&CK framework and better understand your environment based on the data that is active, available, or not yet available in your Splunk environment allowing you to take action and plan for the future.
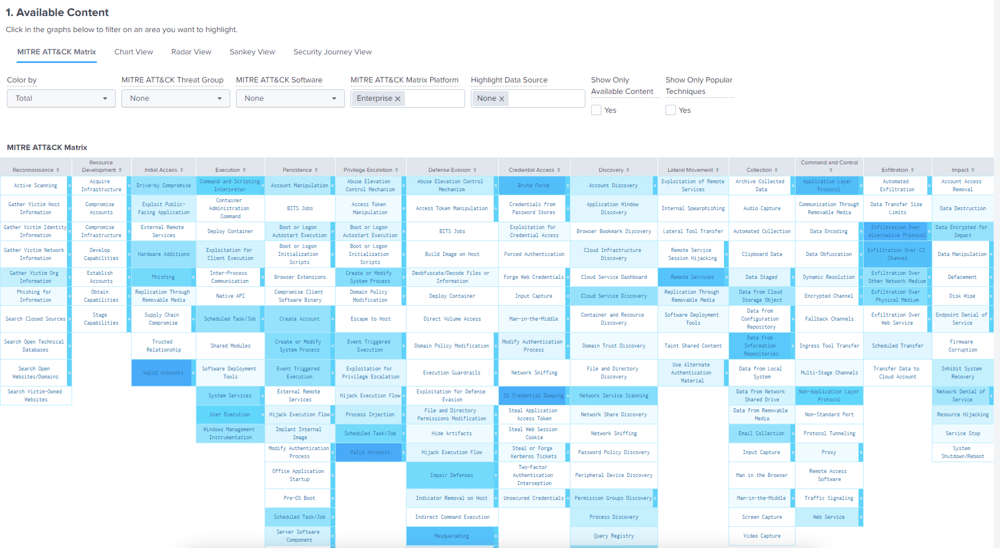
Security Essentials allows you to subdivide your MITRE ATT&CK Matrix against any of the sub-matrices, i.e. Enterprise, Mobile, and ICS etc.
You can also filter on “Show Only Popular Techniques” that filters the ATT&CK Matrix and displays the techniques that 5 or more Threat Groups are associated with. This is a good way of finding the techniques that pose the greatest risk.
Splunk Security Essentials uses bookmarking to track what content is active in your environment which is key to enriching the matrix, content recommendations, ES integrations with Splunk Enterprise Security, Risk-based Alerting RBA, and the Data Availability Dashboard.
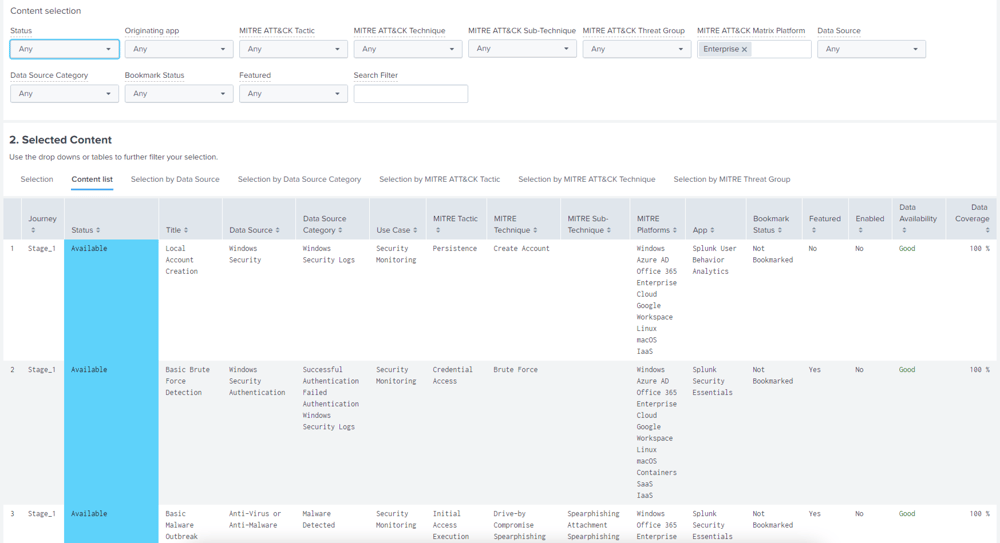
With the knowledge of what data you have, you can specify the types of security concerns you’re facing and then use MITRE ATT&CK to filter for the Splunk content related to MITRE Techniques that are associated with many different threat groups.
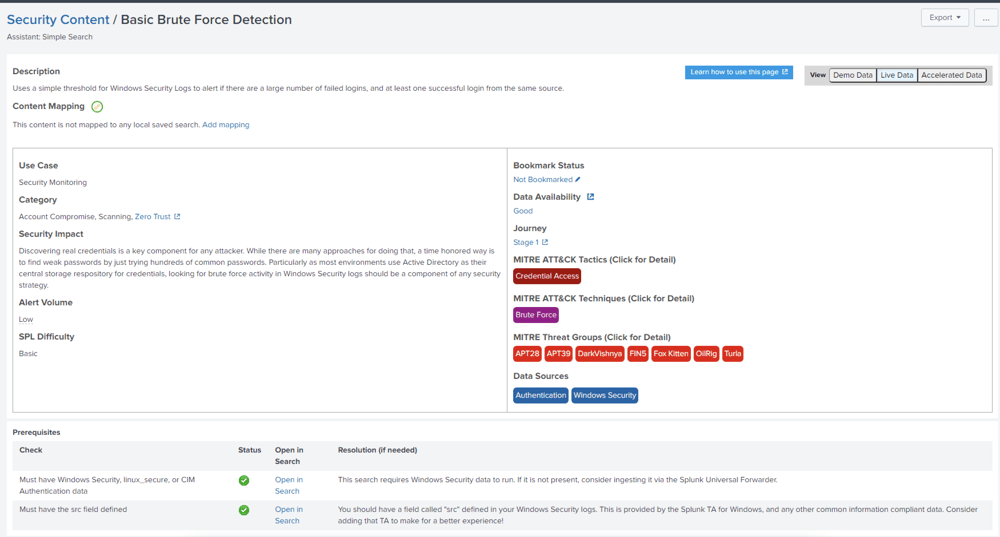
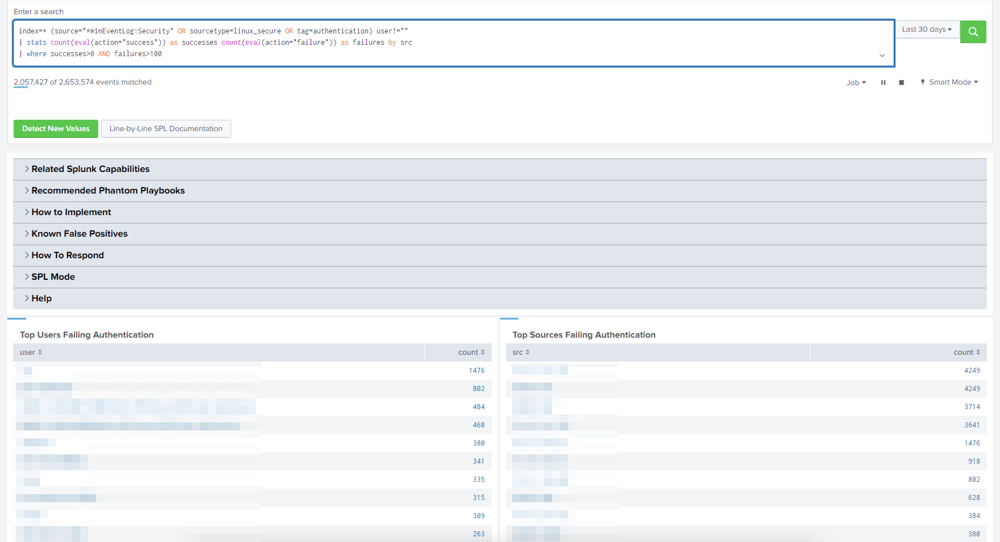
Below is an example of a Correlation Search provided by Security Essentials you can use to implement a particular tactic.
Arcus Data and the MITRE ATT&CK Framework
Splunk and the MITRE ATT&CK framework are a perfect partnership for security teams looking to improve their security practice.
With 100's of Splunk deployments under its belt, Arcus Data is perfectly positioned to help organizations operationalize the MITRE ATT&CK framework unleashing its full potential. Reach out to hello@arcusdata.io for more information.



